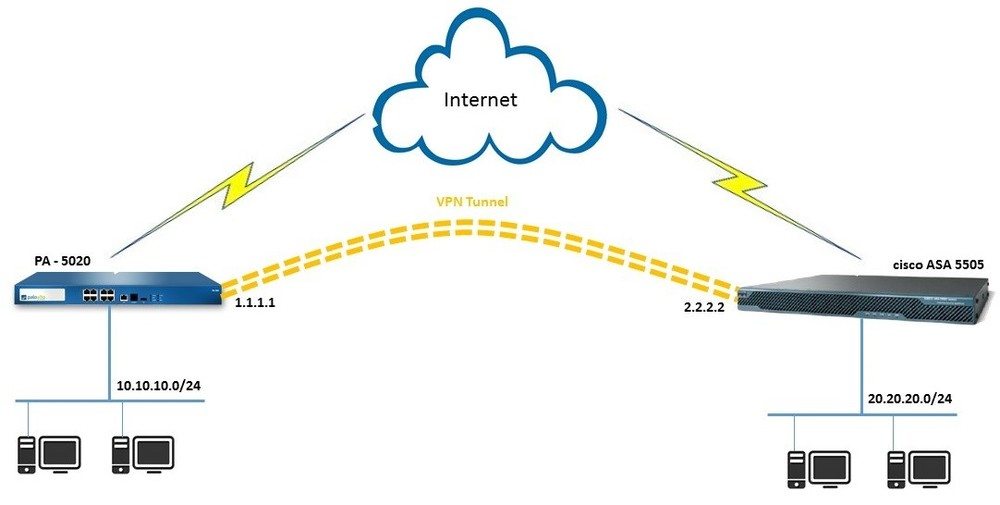
Asa Vpn Site-tosite And One End Nat
Re: site to site vpn tunnel with multiple subnets at one end. I don’t believe the PIX/ASA supports 2 tunnels from the same source IP. Maybe you could just change your subnet mask so it includes. The main goal is to configure a site-to-site IPsec VPN between two sites using an ISR at one end of the tunnel and an ASA at the other end. The final running configs for all devices are found at the end of the lab. Part 1: Basic Router/Switch/PC Configuration.
Site To Site Vpn Configuration On Cisco Asa Command Line
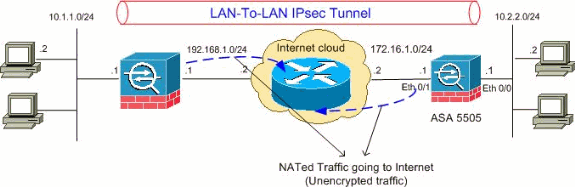
Using the above network diagram, the scripts below can be applied to both ASA’s to build a site to site VPN tunnel. The firewall on the left is a Cisco ASA and device on the right is a Cisco Router. The router needs to have an IOS that supports VPN’s. You can test this by typing ‘crypto?’ and see if it has the commands available to make the tunnel. Usually a router with a K9 image on it is good enough.
If not then it’ll require the security image to have IPSec capabilities.After applying the config below the device at 192.168.11.2 should be able to access 172.16.22.2 and vice versa. !^^^^^^^ ISAKMP (Phase 1) ^^^^^^^!!
The policy number is arbitrary. The parameters inside the policy! Must match with the other side in order for Phase 1 to complete.! Lower policy numbers will likely be used before higher ones.crypto isakmp policy 5authentication pre-shareencryption aeshash shagroup 2lifetime 86400! Enable ISAKMP on the outside interfacecrypto isakmp enable OUTSIDE! Define the pre-shared-keytunnel-group 22.22.22.22 type ipsec-l2ltunnel-group 22.22.22.22 ipsec-attributespre-shared-key sekretk3y!^^^^^^^ IPSEC (Phase 2) ^^^^^^^!!
Define the interesting traffic in the ACLaccess-list ACL-RED-VPN permit ip 192.168.11.0 255.255.255.0 172.16.22.0 255.255.255.0crypto ipsec transform-set ESP-AES128-SHA esp-aes esp-sha-hmac! Create a crypto map entry that defines the tunnelcrypto map MAP-OUTSIDE 20 set peer 22.22.22.22! ACL must be exactly the opposite of the other sides ACLcrypto map MAP-OUTSIDE 20 match address ACL-RED-VPN! Transform set must match other side identicallycrypto map MAP-OUTSIDE 20 set transform-set ESP-AES128-SHAcrypto map MAP-OUTSIDE 20 set security-association lifetime kilobytes 10000! Apply crypto map to an interfacecrypto map MAP-OUTSIDE interface OUTSIDE!^^^^^^^ Routes and No-NATS ^^^^^^^!!
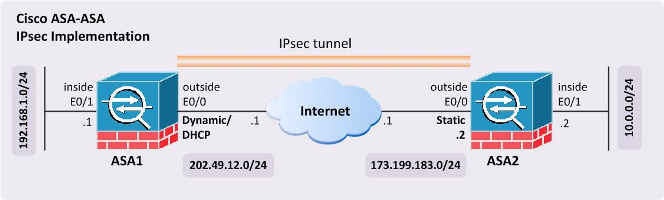
Point the destination network out the outside interface with a next hop as the default gateway.route OUTSIDE 172.16.22.0 255.255.255.0 11.11.11.1! Make sure that the VPN traffic is NOT NAT'daccess-list ACL-INSIDE-NONAT extended permit ip 192.168.11.0 255.255.255.0 172.16.22.0 255.255.255.0nat (INSIDE) 0 access-list ACL-INSIDE-NONATRED ROUTER WITH CRYPTO SUPPORT. !^^^^^^^ ISAKMP (Phase 1) ^^^^^^^!! Note: The default isakmp settings on a router are Encr:DES Hash:SHA DH:Group 1! If these settings are used, they will not show under 'show run'crypto isakmp policy 5encr aeshash shaauthentication pre-sharegroup 2crypto isakmp key sekretk3y address 11.11.11.11!^^^^^^^ IPSEC (Phase 2) ^^^^^^^!! Define the interesting traffic in the ACLip access-list extended ACL-VPNpermit ip 172.16.22.0 0.0.0.255 192.168.11.0 0.0.0.255crypto ipsec transform-set AES-SHA esp-aes esp-sha-hmaccrypto map VPN-TUNNEL 1 ipsec-isakmpset peer 11.11.11.11set transform-set AES-SHAmatch address ACL-VPNinterface Fa0/0crypto map VPN-TUNNELip nat outsideinterface Vlan2ip nat inside!^^^^^^^ Routes and No-NATS ^^^^^^^!! Point the destination network out the outside interface with a next hop as the default gateway.ip route 192.168.11.0 255.255.255.0 22.22.22.1!
Make sure that the VPN traffic is NOT NAT'dip access-list extended ACL-NATdeny ip 172.16.22.0 0.0.0.255 192.168.11.0 0.0.0.255permit ip any anyip nat inside source list ACL-NAT interface Fa0/0 overloadPosted by Jack May 2 nd, 2010,.
